Incidents of cyber crime are typically associated with fraudulent activities exploiting the (in)security of credit card payment schemes or on-line transactions. When these occurrences have affected individual citizens it has been normally attributed to the effort of criminal hackers who infect millions of computers for the purpose of gaining access to information relating to personal financial assets.
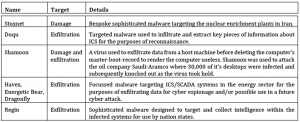
Over time, the victims may change, but the general modality of the crime, monetization by manipulation of transactions, is inherently similar. Attacks on Critical National Infrastructure (CNI) did not have a specific modality attached to them, at least publicly. This changed in 2009 with the deployment of the Stuxnet malware. Targeted attacks from nation states and criminal organizations have subsequently become more common; or at least more widely reported in as being persistent. These activities, often termed Advanced Persistent Threats, have affected many CNIs from aviation to water processing utilities. Energy operators are not exempt and the TABLE below illustrates some examples of recent recorded attacks.
TABLE – Examples of Cyber Attack to Energy Providers
The increasing number of cybersecurity issues has spurred the attention of public policy makers. The US Federal Government (Executive Order 13636) has put forward regulations aimed at protecting the cybersecurity of Critical National Infrastructure (CNI) and translated them into a substantive technical Framework. The European Union has followed suit with a proposal for a specific European Directive in this area.
Managing and regulating cybersecurity issues is particularly relevant for CNI Operators (CNIOs), private or publicily traded enterprises in charge of the bulk transmission of electricity, oil- production and processing or gas- production and distribution.
A pressing question for policy makers is: which is the optimal way to regulate the cybersecurity of critical infrastructure operators in charge of electricity transmission?
Should regulation follow a US style, mostly ‘rules-based’ model, or the EU approach, mostly ‘risk-based’ (from the firm’s perspective), or a balance of both?
The Paper “Economic Impacts of Rules-based versus Risk-based Cybersecurity Regulations in Critical Infrastructure Providers (Bulk Electricity Providers)”[1] discusses about the economic issues behind this choice and presents a cybersecurity economics model for public policy in presence of strategic attackers.
The model shows that optimal choices are subject to phase transitions: depending on the combination of incentives, operators will stop investing in risk assessment and only care about compliance (and viceversa). It suggest that different approaches may be appropriate to different conditions, and that just pushing for more rules may have unintended consequences.